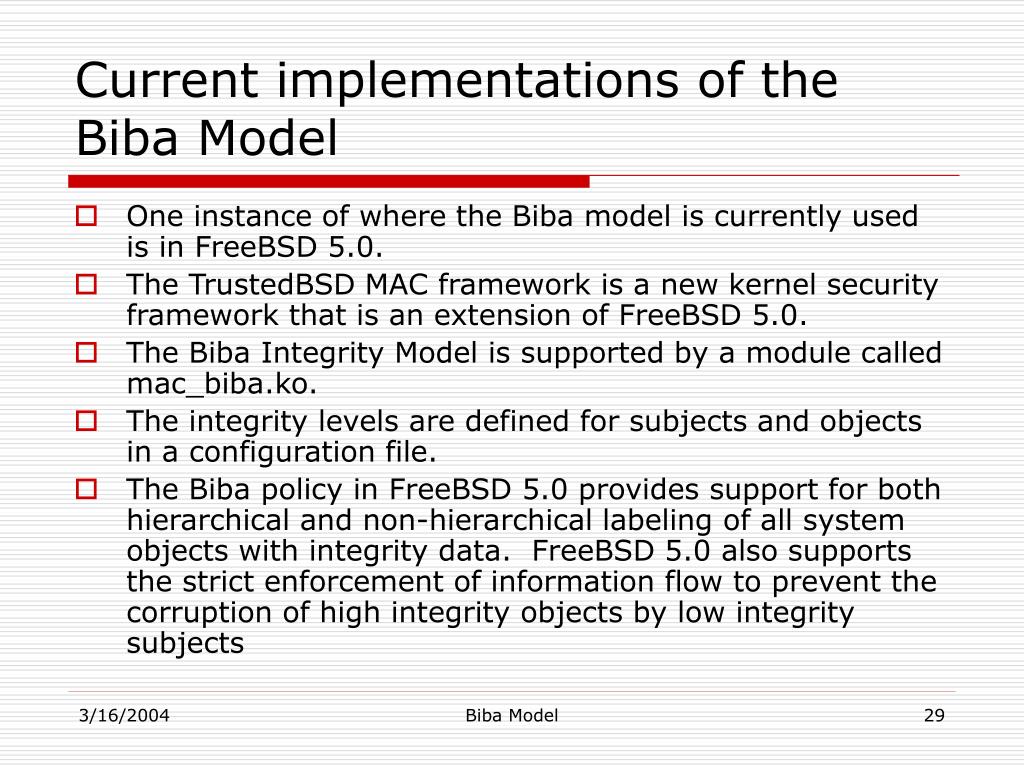
Toxics | Free Full-Text | Environmental Geochemistry and Fractionation of Cadmium Metal in Surficial Bottom Sediments and Water of the Nile River, Egypt

CS426Fall 2010/Lecture 251 Computer Security CS 426 Lecture 25 Integrity Protection: Biba, Clark Wilson, and Chinese Wall. - ppt download
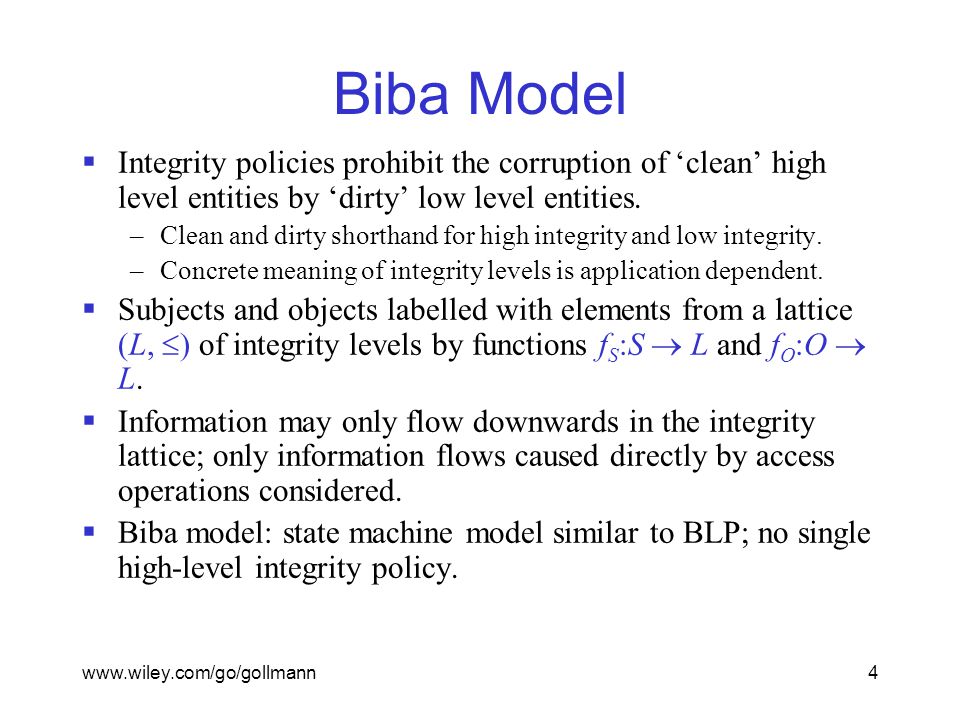
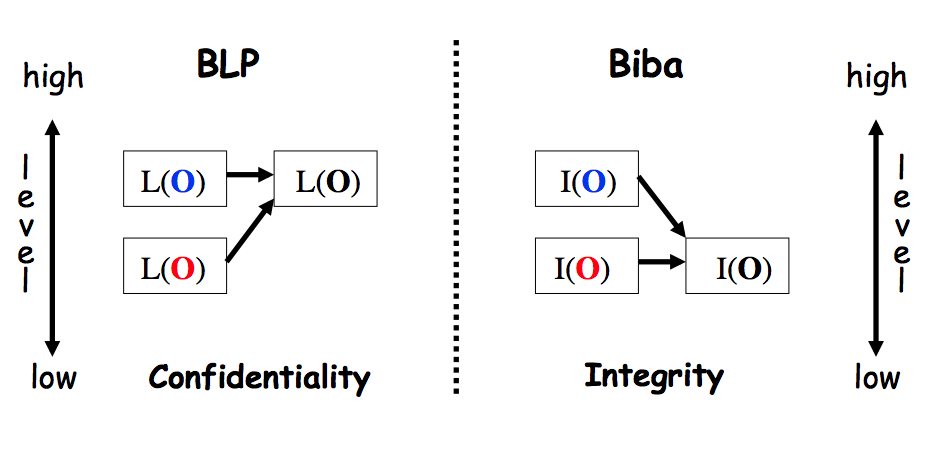
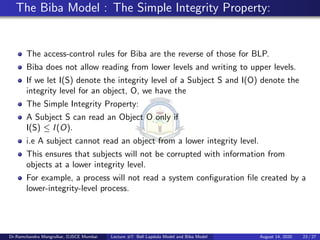
Outline Bell-LaPadula, linear case High watermark property Biba and low watermark Information-flow perspective

9 BIBA Kurta Sets From The Amazon Great Indian Festival Sale-2022 to Doll You Up This Navratri | PINKVILLA

Improved Biba model based on trusted computing - Liu - 2015 - Security and Communication Networks - Wiley Online Library













![PDF] PRIMA: policy-reduced integrity measurement architecture | Semantic Scholar PDF] PRIMA: policy-reduced integrity measurement architecture | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/a5144e59d0a9036885b037ddacbc04effc1405e0/4-Figure2-1.png)